Before we learn how to search for vulnerabilities, we need to have a solid understanding of what a vulnerability in the world of IT is. According to the European Union Agency for Network and Information Security (ENISA), a vulnerability is “the existence of a weakness in the design or in an implementation that can lead to an unexpected, undesirable event compromising the security of the computer system, the network, the application, or the protocol involved.”
Another description of what a vulnerability is comes from the Internet Engineering Taskforce (IETF): “A flaw or weakness in a system's design, implementation, or operation and management that could be exploited to violate the system's security policy.”
A more abstract description of what a vulnerability is could be this: something that makes it possible for someone to force your computer to do something you don’t want it to. Some less abstract examples include the following:
- A web browser plug-in/extension/add-on that allows a malicious website to infect a visiting computer with malware.
- A web service that stores its usernames and passwords in a non-secure way.
- A file share containing secret documents that everyone on the network has access to when they most likely shouldn’t.
- A public web server with the poorly chosen password of 12345678 for its administrative interface.
In my book, I went through a number of ways of how to successfully test computer systems for the vulnerability examples listed above (along with many more examples and techniques).
Regardless of how you chose to define a vulnerability, you might be requested to describe its possible impact from a CIA perspective. CIA stands for confidentiality, integrity, and availability. The acronym is used to describe the fundamental building blocks of information security.
Confidentiality aims to prevent sensitive information from falling into the wrong hands. Credit card data, medical records, and usernames/passwords are three examples of such information. When the confidentiality of a system has been violated, the information owner must (or a least should) do her very best to limit the damage done.
Integrity seeks to prevent information from being altered by unauthorized users. An example would be an online e-commerce system where a customer can view, and change, the order information of other customers without leaving any trace of doing so. When the integrity of a system has been violated, the information it processes can no longer be fully trusted.
Availability aims to keep information accessible when it is needed. Power outages or distributed denial of service (DDOS) are two examples of how the availability of a system can be affected. When the availability of a system has been violated, the system can no longer perform its intended function.
The idea behind the CIA concept is that all three aspects must be taken into consideration while trying to maintain an acceptable security level. Not all three aspects are equally important for every kind of system, and some systems may do just fine without one or even two of them, but system owners should always consider all three.
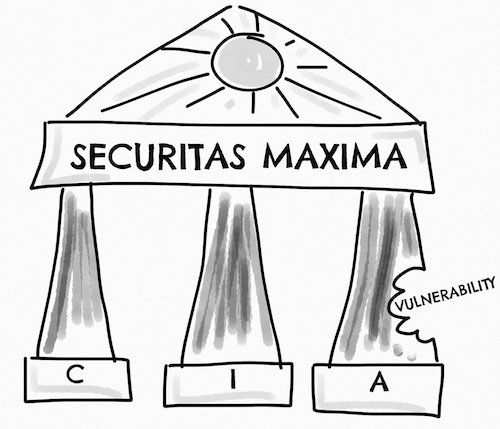
An illustration of the importance of the CIA concept can be seen in the image below. The once rock-solid palace of Securitas Maxima is about to become a ruin because of the vulnerability that is eating away the stability of the Availability pillar. Even though the other two pillars are still intact, the system as a whole can no longer perform its intended function if the damaged Availability pillar is left unattended.
While the CIA acronym is arguably the most common way of describing the fundamental parts of information security, other models exist to describe more or less the same thing.
Two alternatives are the Parkerian Hexad and the security goals of RMIAS.
Worth noting also is that CIA is sometimes described by its opposite: disclosure, alteration, and destruction (DAD).
Robert Svensson
Tags: #vulnerability #C.I.A. #confidentiality #integrity #availability
2017-10-30 11:10:00